Get my OWASP course with 90% discount on Udemy.Use coupon code: HACKYTDis a demo. Enjoy the videos and music you love, upload original content, and share it all with friends, family, and the world on YouTube.
In today’s write-up we’re going to take a look at getting into Hack the Box’s retired Netmon machine, which was a relatively easy box if you just remembered that people tend to have bad password habits.
Recon
We start with an nmap scan which gives us quite a few open ports:
What immediately catches the eye is the ftpd which allows anonymous access on what appears to be the root directory. But before we start exploring this further, let’s have a quick look at port 80 to confirm the nmap result.
We see the PRTG bandwith monitor web app running and can also confirm the version information in the lower left:
Googling for default credentials gives us prtgadmin:prtgadmin, however, these don’t work ¯(ツ)/¯.
Looking for exploits
Doing a searchsploit search for PRTG, we find two exploits matching the running version – one of them for Denial of Service, the other one for an authenticated Remote Code Execution:
Denial of Service is not what we want and the RCE will only work if we have valid credentials for the PRTG web interface.
Enumerating FTP
Let’s look at what the anonymous FTP access can give us, and while looking around, do another nmap -p- 10.10.10.152 to scan all TCP ports, so that we have something to come back to after the FTP enumeration.
While we cannot write files, we seem to have pretty wide read access. So much indeed, that we can directly snatch the user.txt flag at /Users/Public/.
As we can access /Windows/System32, we can also verify the OS version (license.rtf mentions Windows 2016 – different than what nmap reported), which might be handy later on.
Having the promising RCE in PRTG Network Monitor in the back of our minds, let’s see if we can find configuration data that might give us access to the web interface.
Googling around, we quickly find How PRTG Network Monitor Stores its Data, which tells us:
Windows Server 2012 (R2), Windows Server 2016, Windows 10, Windows 8.1, Windows 8, Windows 7, Windows Server 2008 R2: %programdata%PaesslerPRTG Network Monitor.
… and:
| PRTG Configuration.dat | Monitoring configuration (i.e. probes, groups, devices, sensors, users, maps, reports, etc.) | XML |
| PRTG Configuration.old | Backup of previous version of monitoring configuration | XML |
So let’s have a look at these and other config files at /ProgramData/Paessler/PRTG Network Monitor.
To make the process of grepping through the files faster (as we don’t know exactly where and how PRTG Network Monitor stores files), we can actually download the whole folder: wget -m ftp://10.10.10.152/ProgramData/Paessler (about 14 MB).
Doing something like grep -r . -A1 -ie 'password' in this folder gives way too many hits, so let’s narrow down on the PRTG Configuration.old.bak first, as this isn’t a standard file and .bak files are generally interesting for findings.
Microsoft Ftpd Exploit Rapid7
grep 'PRTG Configuration.old.bak' -A2 -ie 'password' | less reveals right at the top a username and password:
Exploitation
Trying the password over at http://10.10.10.152 we still get Your login has failed. Please try again!.
Thinking of bad password habits, though, we might guess that the password could still be the same but with a changed year suffix (as this one was found in an old backup file).
prtgadmin:PrTg@dmin2019 works immediately and we are greeted by the welcome screen:
Guessing the password year increment reads easy here, but it actually had me stuck longer than it should have :-)
Having access, we can now look at the exploit we found earlier via searchsploit.
Examining it via searchsploit -x 46527 and reading a blog post of the vulnerability, we can see that it does command injection via a notification feature (by using a demo ps1 script) and through that adds a new administrative user to the machine.
As this is not the stealthiest way, let’s see if we can exploit it in a slightly different way without adding a new user.
In Setup -> Account Settings -> Notifications, we can add a new notification and enable the “Execute Program” option as described in the above blog post. There, we find the two demo scripts and the “Parameter” field which we can (ab)use to add another command of our own, right after the argument to the demo script.
At first, let’s try to do a simple ping to the attacker machine:
And on the attacker machine:
After clicking the “bell” icon on the right to send a test notification, the ICMP packet arrives, meaning we successfully injected the ping command.
To now get a reverse shell, we can grab a Powershell one-liner from the excellent swisskyrepo Reverse Shell Cheat Sheet, and use this instead of the ping:
All we need to do now is change the IP to our own, the port to 80 and start a netcat listener via nc -lvnp 80. Sending another “test notification” then gives us a shell. And since PRTG Network Monitor is running as System, we are as well:
Cheers!
I hope you’ve enjoyed this write-up. If you have any questions, did it another way or have something else to say, feel free to leave a comment. I’m always happy to learn new things. You can also check out the other write-ups.
Hello everyone! Welcome to another writeup in the HacktheBox writeup series. In this writeup, we will discuss the Windows machine ‘Remote’. The Remote machine is officially retired from HackTheBox. Let’s go and PWN this.
Information Gathering:
Nmap:
As usual, we will start the machine with Nmap to establish open Ports in our target and also to find the services running on those ports.
Here we got our results. There is a total of 8 ports.
- Port 21 – Anonymous access allowed for FTPD service.
- Port 80 – It seems to be an HTTP web page.
- Port 111 – RPCBind is also called as PortMap. It enables a Unix system to find Unix compatible services in a Windows system.
- Port 135 – MSRPC – Client/Server model by default.
- Port 139 – Netbios SSN – A session dependent communication.
- Port 445 – SMB Service.
- Port 2049 – Seems like NFS is running. We can use this to access site_backups.
- Port 5985 – WinRM – Windows Remote Management utility service.
Apart from these, Port no. 21 and 80 stood out.
FTP Enumeration:
Since FTP allows anonymous login, we can check if there is any key given for the lock.
Sadly, we got nothing from FTP. Let’s check the Webpage now.
Web Enumeration:
We were welcomed by a widget page as the main page.
There is nothing useful I found on the web page except some usernames and the name of CMS ‘Umbraco’.
Mountd Enumeration – Site Backups – Credential:
As we haven’t got anything useful on the web page, we can check the Mounted NFS.
This seems to be the backup of the website we visited earlier. Let’s enumerate further on it.
After some enumeration, we found a Hash for user ‘admin’ of Umbraco CMS. Let’s crack it.
Hooray! We got the credential for Umbraco CMS [email protected]:baconandcheese.
Umbraco CMS – Public Exploit – RCE – User Shell:
Google resulted in a lot of articles on how to exploit Umbraco CMS 7.12.4. With an authenticated credential, one can gain RCE easily.
Reference 1: Umbraco Authenticated RCE
Wow! It is working. Let’s upload NC for the reverse shell.
Now, its time to fire NC to catch the shell in the listener.
Boom! We got the ‘apppool’ shell and owned the User flag.
UsoSvc Servicce Abuse – Administrator:
Running WinPEAS.exe gave a way to elevating privileges.
The above means our user can modify settings and restart the UsoSvc service. Let’s create a reverse shell exe file and update the UsoSvc’s binary to our malicious one and restart.
Our malicious payload is ready to launch. Let’s update the binary path for UsoSvc.
Now all set. Before restarting the service, I set up my listener to catch the shell.
On checking the listener, I got the Administrator and can read the Root flag too.
Voila! We just owned the Machine. There is one more way to root the machine using the MSF module.
MSFConsole – Local Password Disclosure – TeamViewer 7:
WinPEAS.exe reveals the version of TeamViewer 7. Since it is an older version, I searched for public exploits and found that this version is vulnerable to Local User’s Password Disclosure. Admin may be lazy to use different passwords for different services.
Microsoft Iis Httpd Exploit
Reference 2: Rapid7 MSFModule
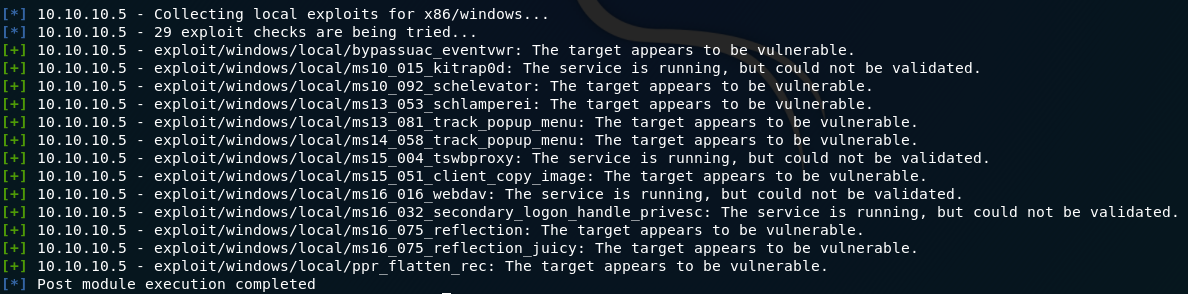
To run this, we need to get a meterpreter shell.
Uploading this payload and executing it to get the meterpreter shell.
The Meterpreter shell is opened and it is backgrounded in order to run the post exploit module.
Reference 3: Module for TeamViewer
We got a credential stored in Registry which has been used by TeamViewer software. Let’s use this against the Administrator.
Boom! It’s worked. Again we read the Root flag with the Evil-Winrm tool.
The Machine is Rooted 😉

Hope you all enjoyed the write-up. If you have any queries or feedback, please leave it in the comment section. This is My Story from Chemical Engineer to InfoSec. Meet you guys in the next writeup.
